Turkey Express Mini CTF 🦃
Table of Contents
Instructions #
- “Your goal for each challenge is to find a “flag.” A flag is a string of text that will usually, look like this:
MetaCTF{some_phrase}. The grader is pretty lenient, submissions are case insensitive, and it doesn’t care if you use the MetaCTF{} brackets.”
Challenges #
Welcome to the Obfuscation Games #
Category: Reverse Engineering
During a recent incident response investigation, we came across this suspicious command executed by an attacker, and we’d like you to analyze it. Malware authors like to obfuscate their payloads to make it harder, but we’re sure you’re up to the task. See if you can figure out what’s happening without even running it!
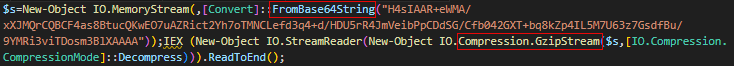
$s=New-Object IO.MemoryStream(,[Convert]::FromBase64String("H4sIAAR+eWMA/xXJMQrCQBCF4as8BtucQKwEO7uAZRict2Yh7oTMNCLefd3q4+d/HDU5rR4JmVeibPpCDdSG/Cfb042GXT+bq8kZp4IL5M7U63z7GsdfBu/9YMRi3viTDosm3BlXAAAA"));IEX (New-Object IO.StreamReader(New-Object IO.Compression.GzipStream($s,[IO.Compression.CompressionMode]::Decompress))).ReadToEnd();
Walkthrough
From the given PowerShell syntax, we can see that there is a Base64 encoded string compressed with Gzip.
We can reverse the compression and encoding process with CyberChef
From Base64->Gunzip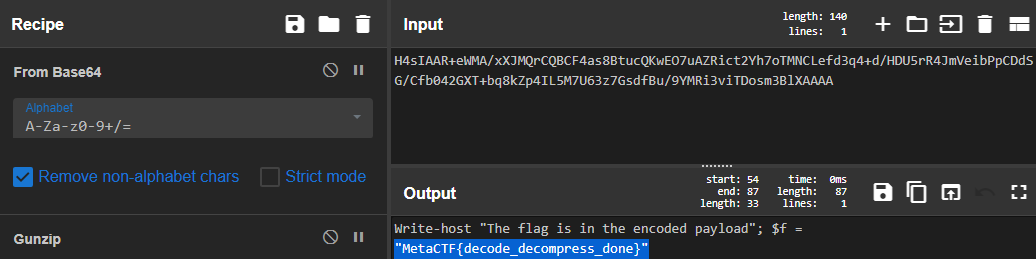
Answer: MetaCTF{decode_decompress_done}
Staging in 1…2…3… #
Category: Forensics
The Incident Response (IR) team identified evidence that a Threat Actor accessed a system that contains sensitive company information. The Chief Information Security Officer (CISO) wants to know if any data was accessed or taken.
There was a suspicious file created during the timeframe of Threat Actor activity: C:\xyz.tmp. Can you check it out?
Walkthrough
Working with a new Kali VM and CTF working directory, we can use curl to download the suspicious file
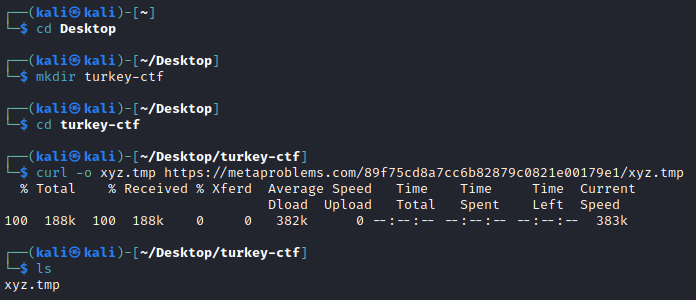
We can us the
filecommand to verify the fyle type, which reveals that this file is actually a 7-zip archive.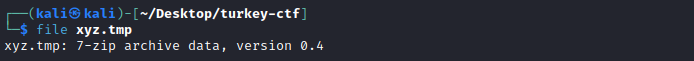
Let’s rename the directory with the
.7zfile extension, then extract the contents withp7zip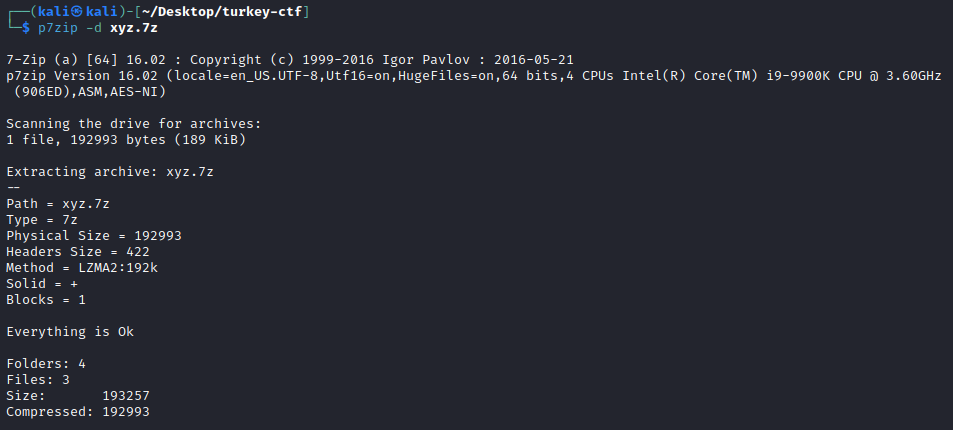
List out our extracted contents to reveal the flag with
ls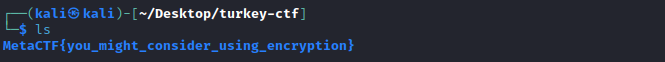
Answer: MetaCTF{you_might_consider_using_encryption}
The Impossible Survey #
Category: Web Exploitation
Your company just developed a new product, and before releasing it to the public, they decided to gauge the reactions from their employees through a survey. As an incentive, the participants get a gift card after completing it. A company-wide email was sent a while ago, yet no one has submitted the survey or claimed the gift card code.
Can you be the first one?
- Hint: The website is using strong input validation
Walkthrough
The link provided in the question goes out to a survey through Google Forms.
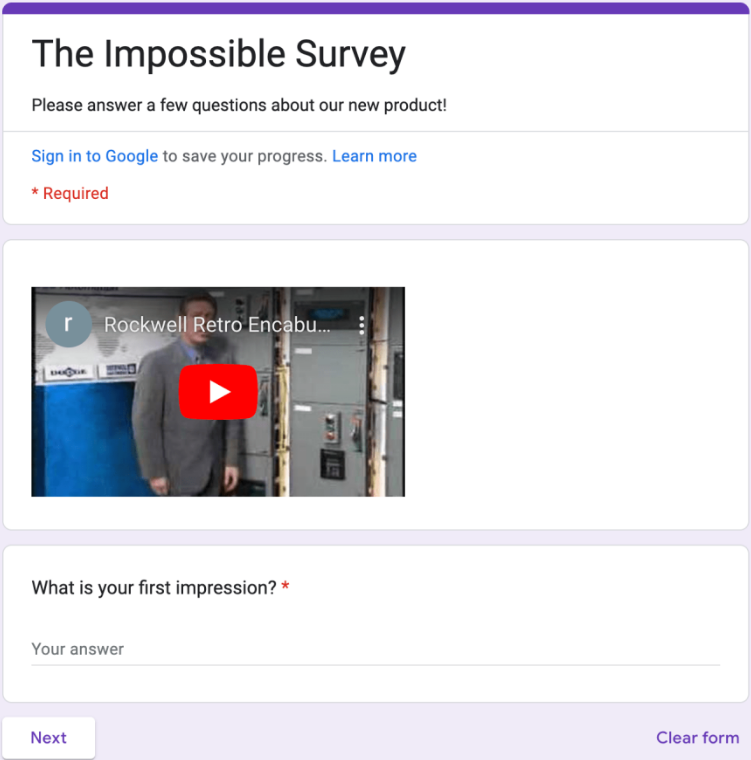
Trying to answer normally, I couldn’t get the survey to accept my answer. I kept receiving the same error:
Too short (need at least 50 characters)I entered in a response that was over 50 characters, but got the same error again.
I decided to inspect the source code and found that all of the survey questions were located in there, along with the flag.
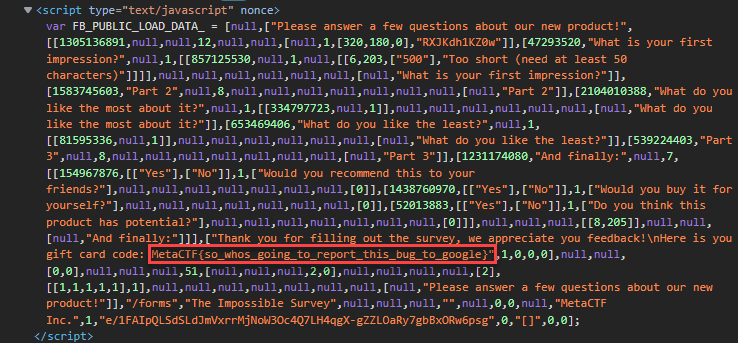
Answer: MetaCTF{so_whos_going_to_report_this_bug_to_google}
Diving Into the Announcement #
Category: Reconnaissance
Vulnerabilities are patched in software all the time, and for the most serious ones, researchers work to build proof-of-concept (POC) exploits for them. As defenders, we need to continuously monitor when new public exploits drop, figure out how they work, and ensure we’re protected against them. At some point, Microsoft announced CVE-2020-1472. Your task is to locate a public exploit for it and identify the vulnerable function that the POCs call. The flag will be the function’s name.
- Hint: Focus on the function that changes the password
Walkthrough
During my initial search, I went down the path of finding actual exploits and vulnerability detection methods, but didn’t recognize aything describing the proof of concept. CVE-2020-1672
I came across a CrowdStrike article that described the attack flow and the Windows function leveraged in the exploit, which we can submit as the flag: Zerologon (CVE-2020-1472): An Unauthenticated Privilege Escalation to Full Domain Privileges
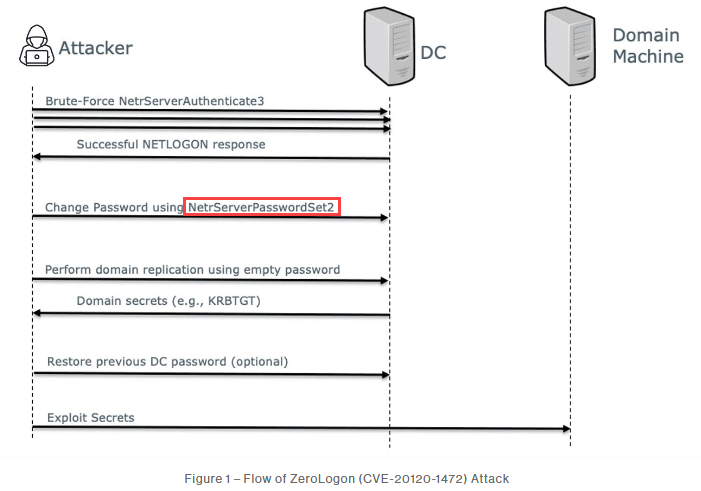
Answer: NetrServerPasswordSet2
A Confident Hash #
Category: Other / Offline Password Cracking
Check out this hash. Can you crack it? Here’s a wordlist you can use. You only have 5 attempts to get the flag right.
$2a$04$KMCaaiytS5OIsg2UZtthzugkZUPDqQ/Zyoys8XAY6AJVgirU/MWOS
Walkthrough
This looks like a password hash from
/etc/shadow. A quick Google search showed that the $2a prefix is for abcrypthash.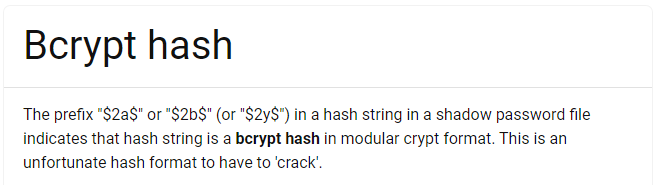
We can download a copy of the wordlist with
curland save it in our working directory
With the hash and wordlist ready, we can set up our dictionary attack using
hashcat.We need to find the corresponding numerical code for bcrypt in hashcat (3200). grep for bcrypt in the help page:
hashcat --help | grep bcrypt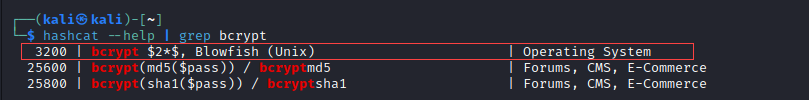
cdto the working directory containing the hash and wordlist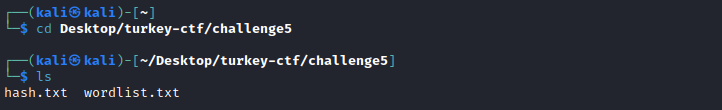
Set up hashcat and start cracking!
Using a workload profile of 3
-w 3gives a nice balance of computing power while maintaining GUI access.Attack mode zero
-a 0will use the wordlist as-is to crack hash mode 3200-m 3200Store the output results in a file called cracked.txt
-o cracked.txtto reference laterSpecify the
hash.txtto crack andwordlist.txtas the dictionaryhashcat -w 3 -a 0 -m 3200 -o cracked.txt hash.txt wordlist.txt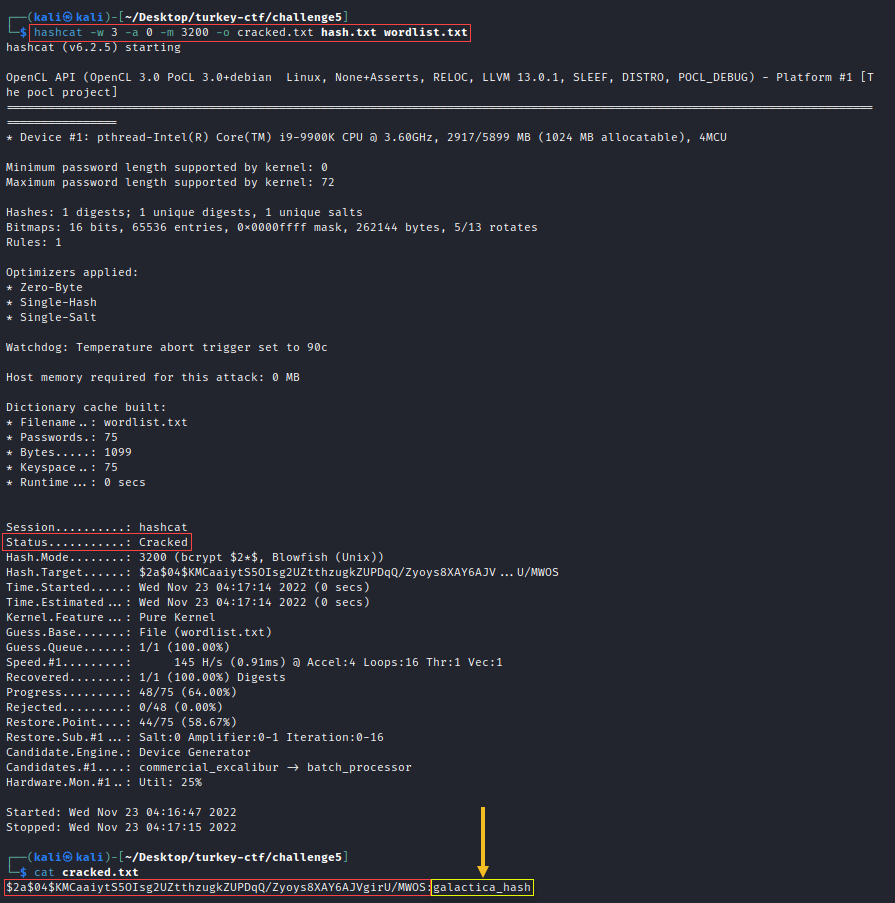
Answer: galactica_hash
King to Queen 3 #
Category: Cryptography
An employee on the network has been emailing these chess puzzles everyday to someone outside of the domain, and nobody really thought it was suspicious until they saw this weird string sent to that same person on the following day: F^mY;L?t24Zk.m^-hnWl,[l)[ku
The SOC team has provided an archive of the email attachments, and has tasked you to investigate the actual contents of the ciphertext. Can you figure out what they’ve been saying?
Hint: The flag is wrapped in
MetaCTF{}. This should be enough to help you figure out the encoding.Combined email image archive:

My Approach / Solution
I eventually landed on the answer to this one. Instead of a walkthrough, I documented my process because I ultimately tried several combinations before getting the answer.
Starting out, I tried running different forensic/steganography-related linux commands against the images to see if there was any hidden information in the metadata or raw data, but didn’t find anything noteworthy.
- I even filtered based on the file’s original creation time (File Modification Date/Time) to see if there was relevance or a clue based on that order - Each file was created in order as they were named (1-9.png) and didn’t seem to have any significance.
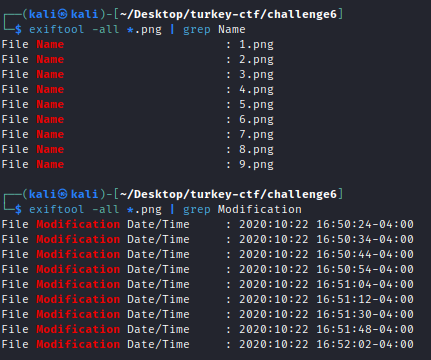
- I even filtered based on the file’s original creation time (File Modification Date/Time) to see if there was relevance or a clue based on that order - Each file was created in order as they were named (1-9.png) and didn’t seem to have any significance.
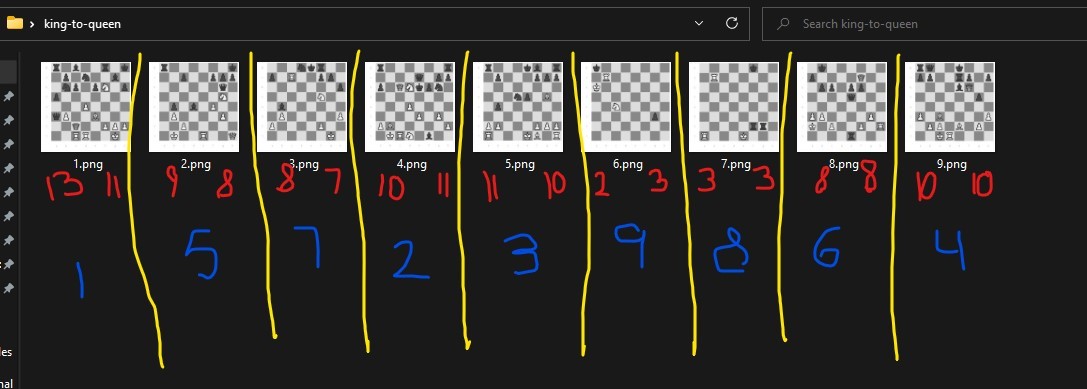
Next, I tried reordering the images based on the number of pieces left on the board as they appear in each image, thinking that might give a clue to what the key is… Still no luck.
In the screenshot below, the left red number indicates the number of black pieces, the right red number indicates number of white pieces on the board for each image. The blue number would have been the correct order of the images if they followed the flow of the game based on number of pieces eliminated
I finally tried plugging the ciphertext into the autodetect function at https://www.dcode.fr. It suggested using an ascii shift cypher. Using the hint that the flag was wrapped in
MetaCTF{}, I was able to determine the starting and endpoing point; and that each set of letters were in groups of three. (there are a total of 27 letters in the cyphertext and 9 images, groups of three was promising)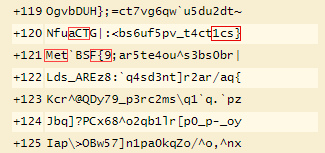
Even with the start and end points, I may have missed a clue somewhere that would have helped identify a pattern. The overall shift didn’t seem to repeat (at least that I could find). Fortunately the ciphertext rotation contained the answer in 1337 words and was on adjacent lines where I could eventually piece together the flag.
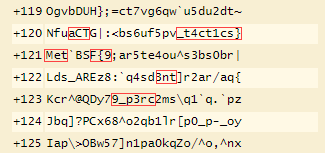
Answer: MetaCTF{99_p3rc3nt_t4ct1cs}
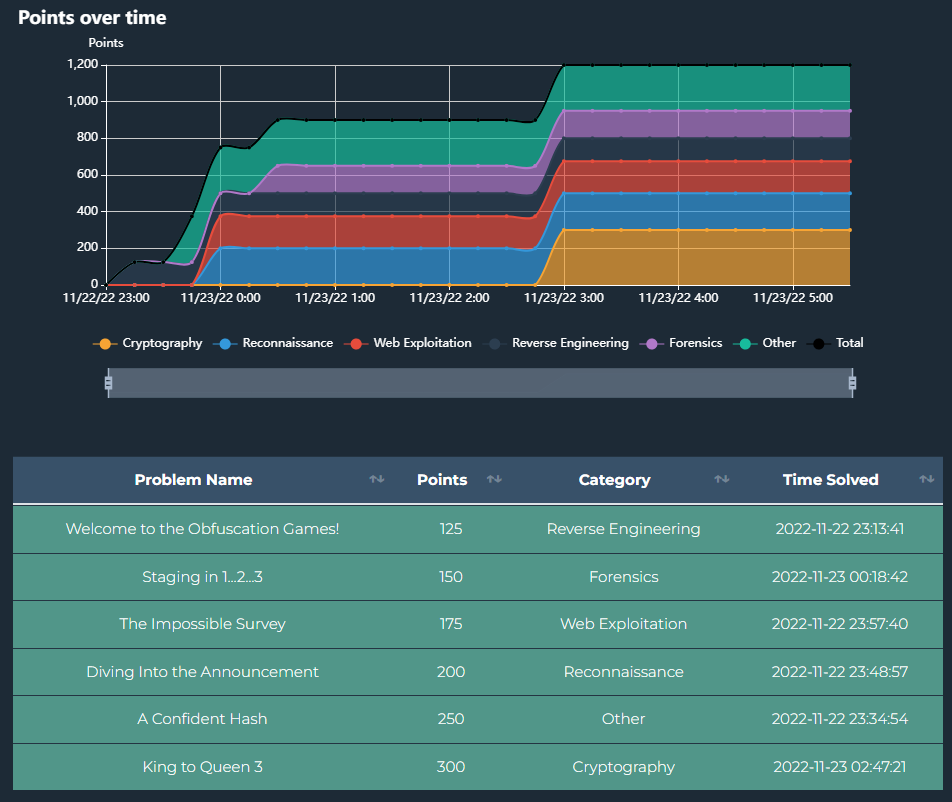
Scoreboard & Stats #
It took me roughly 5 hours to solve and fully document each challenge. I came in 123rd place, which I was happy with. As a beginner-friendly CTF, I completed each challenge, learned a few things, and enjoyed the event.