Huntress CTF 2024
·1 min·
0
·
0
·
Table of Contents
Setting the stage for the Huntress CTF 2024!
Base64by32 #
This is a dumb challenge. I’m sorry.
Solution Walkthrough
The hint is in the name on this one. If we cat out the file, there are thousands of lines of base64 encoded text. We can write a quick for loop in bash to send the file content through 32 rounds of decoding and reveal the flag.
#!/bin/env bash file="base64by32" content=$(cat "$file") for i in {1..32}; do content=$(echo "$content" | base64 -d) done echo $content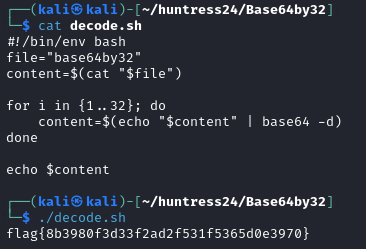
Answer:
flag{8b3980f3d33f2ad2f531f5365d0e3970}
